Red Team – what is it and how does Red teaming work?
Cybersecurity is a rapidly evolving field. With new technologies, constantly changing network architectures, and increasingly complex operating systems, cybercriminals are continuously adapting their tactics. This constant change calls for ongoing testing and analysis of vulnerabilities in applications, systems, and entire network infrastructures.
Table of contents
- What is a Red Team?
- What does Red Teaming involve?
- What can be the target of a Red Team exercise?
- Benefits of Red Teaming
- When should you engage a Red Team?
- How often should Red Team testing be conducted?
- Summary
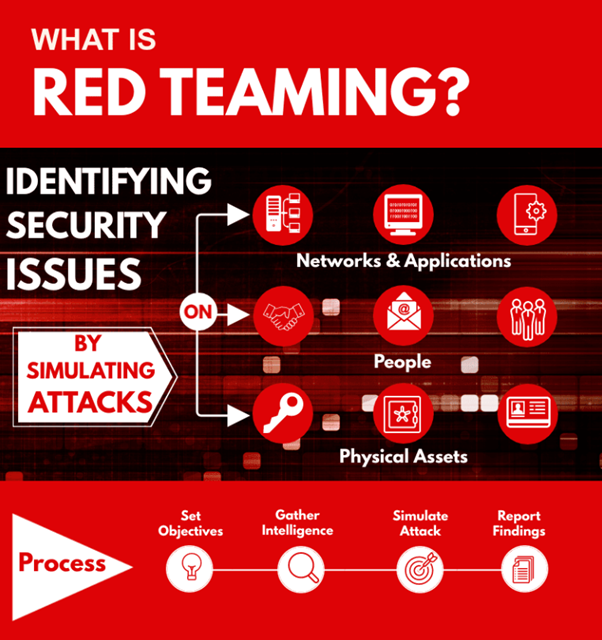
What is a Red Team?
According to the U.S. National Institute of Standards and Technology (NIST), a Red Team is a group of individuals authorized and organized to emulate potential threat actors. In simple terms, they simulate real-world cyberattacks on your systems—targeting your networks, servers, and software as if they were actual attackers.
The primary goal of Red Teaming is to improve an organization’s overall cybersecurity posture by identifying and exploiting weaknesses in complex IT infrastructures before real attackers can.
Source: https://plextrac.com/blog/what-is-red-teaming/
Red Teaming – what is it all about?
The definition of Red Teaming is simple. It’s a form of ethical hacking performed by qualified specialists targeting systems, applications, or computer networks.
Security experts who are part of a Red Team mimic the tactics, techniques, and procedures (TTPs) commonly used by cybercriminals to steal data from servers or gain unauthorized access to software.
In practice, Red Teaming involves:
- Simulating common types of cyberattacks, such as phishing, social engineering, or attempts to extract access credentials;
- Testing human vulnerability through social engineering—for example, by checking if employees reveal confidential information to third parties;
- Monitoring network traffic to uncover sensitive information about IT systems, such as user data;
- Bypassing authentication mechanisms—specialists attempt to crack even strong passwords and two-factor authentication to identify possible flaws in the code.
Another key activity is direct attacks on software APIs. These allow for testing how well developer interfaces are protected against unauthorized access.
In Europe, the most important regulation in cybersecurity is the NIS2 Directive. It provides a unified legal framework for enforcing cybersecurity standards across 18 critical sectors.
In practice, NIS2 mandates regular audits and continuous monitoring of cybersecurity practices in organizations. This means that testing must be conducted cyclically, not just once.
What can be targeted during Red Teaming exercises?
Red Teams may target the following during simulated attacks:
- AI-powered systems;
- Physical workstations, mobile devices, or even server hardware;
- Cryptographic systems;
- Firewalls;
- Web applications;
- SOAR systems (Security Orchestration, Automation, and Response).
Red Teaming helps strengthen cybersecurity foundations in both public and private organizations. CART (Continuous Automated Red Teaming) enables ongoing assessments of current cybersecurity practices and defenses.
Automating testing processes helps reduce operational costs of managing cybersecurity within organizations.
Benefits of Red Teaming
Simulated attacks executed as part of Red Teaming can significantly improve cybersecurity posture across banks, public institutions, and enterprises using advanced IT systems.
Key benefits include:
- Comprehensive assessment of cybersecurity defenses – Realistic testing simplifies the implementation of security improvements and helps develop more effective defense strategies.
- Faster identification of vulnerabilities – Red Team tests can reveal technical issues, such as flaws in code structure.
- Improved incident response readiness – Red Team scenarios challenge Blue Teams responsible for defending against attacks.
- Development of realistic threat scenarios – Simulated threats help organizations create actionable response strategies that can effectively block future cyberattacks.
Red Teaming can also be used to assess cybersecurity risks in SCADA systems (supervisory control and data acquisition) and PLC devices (programmable logic controllers).
Did you know?
According to the Cybersecurity in Polish Companies 2024 report, up to 95% of respondents fear a cyberattack. Meanwhile, 91% admit to using corporate devices for personal tasks—an alarming practice that weakens enterprise security.
When should you consider Red Teaming support?
Red Teaming is particularly useful when:
- Deploying new IT infrastructure or applications;
- Training staff on cybersecurity using real-life scenarios;
- Assessing your organization’s readiness to handle cyberattacks;
- Responding to a data breach and aiming to prevent recurrence.
Testing is also recommended when threat landscapes in your industry evolve—cybercriminals constantly adapt to emerging technologies.
How often should Red Teaming be performed?
Red Teaming is an effective way to evaluate your organization’s preparedness for cyber threats. It involves simulating attacks to uncover security gaps and assess how well your team reacts to real-world scenarios.
It not only helps detect vulnerabilities but also boosts employee awareness—especially in organizations where staff use company hardware for personal needs.
Ideally, Red Teaming should be conducted regularly—once per quarter or at least twice a year.
This ensures your organization remains one step ahead of attackers who are constantly refining their techniques.
One last thing:
Security mechanisms that were effective six months ago may already be outdated today.
One test is not enough. Cyber threats evolve fast, so your defensive strategies must evolve, too.
Sources:
- https://csrc.nist.gov/glossary/term/red_team
- https://www.cnss.gov/CNSS/issuances/Instructions.cfm
- https://www.ibm.com/think/topics/red-teaming
- https://assets.kpmg.com/content/dam/kpmg/pl/pdf/2024/02/pl-Raport-KPMG-w-Polsce-Barometr-cyberbezpiecze%C5%84stwa-2024.pdf
- https://digital-strategy.ec.europa.eu/pl/policies/nis2-directive
- https://vecto.pl/raport-2024