The article below is purely educational. The author presents solutions, that can assure safe browsing if used for legal purposes only. Utilising the tools listed below in illegal ways might cause criminal liability.
While using the internet, we tend to think we’re anonymous in the digital environment. No physical contact, name hidden under an alias, custom email address. These are the elements that make us feel isolated from the rest of the users. It might look like our inline alter-ego is inaccessible for others. Well, it’s not. Surfing on the waves of the internet leaves traces – very specific and accurate information about our persona. The actual us, sitting in front of the computer.
Nonetheless, there are some solutions that allow us to utilise anonymization techniques. If used responsibly, they’ll make us unrecognized and tracing who we are and where we’re from will be significantly harder, sometimes even impossible. There are many ways of anonymization and the toolset that you use depends on the situation we’re planning to be at.
The traces we leave
In the article below I’m going to present commonly available solutions, that are worth to use during everyday online activities. I’ll also focus on behavioural approach, trying to maximize the potential of anonymization by raising awareness of how to think and behave.
Before we proceed to technical solutions, we should learn the ropes. If a person wants to stay undisclosed on the Internet, a certain behavioural pattern should be implemented:
- plan your actions,
- select the right tools,
- be consistent in what you do,
- don’t get outsmarted.
As I’ve mentioned before, every internet user leaves prints. They’re inevitable and critical for proper functioning of the world wide web. It’s caused by a multitude of reasons. Operators that offer access to the web must assign an IP address to a user. It’s an individual address that allows data transfer between certain devices and makes the data travel precisely where channelled. An IP address is assigned automatically and it’s written in system’s Event Log at the beginning of every session. It’s inseparable from the user during the whole session, therefore it stays in the memory of every page we’ve visited. Comparing the information from the provider and the receiver side may compromise the user’s identity and the data he downloaded.
The data we leave while using the web without using anonymizing solutions:
- IP address
- date and time of our visit
- information about the device we use, its operating system and browser
- queries we type in the browser
- data we share in unsecured sources
- our geolocalization
Now that we know what do we want to conceal, let’s proceed to the main point. How to stay anonymous to assure safe browsing?
The safe browsing toolbox
VPN (Virtual Private Network)
It’s a so-called tunnel network, through which the network is channelled between end users. That architecture makes the network transparent for the transferred data packets. The tunnel connects the user’s device directly to the server, that sends data without collecting information about the user. There is no go-between, that could intercept the data. At the same time, data transmitted through the VPN channel is properly encrypted and compressed for the highest transfer quality. The operator sees, that there is data transmitted, but he doesn’t know any specific information.
The technical construct looks as follows:
- a query from the provider reaches the anonymizing service
- the service decrypts the query
- the query is being masked by proxy or NAT routing
- decyphered page call has a new IP address and it’s the anonymizing service address, not the one of the user
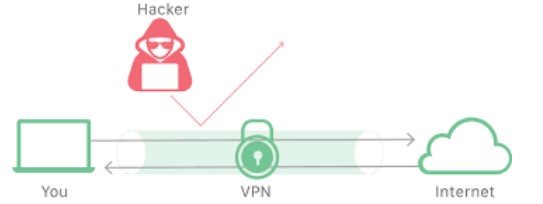
Fig. 1 VPN network architecture
While choosing the VPN service provider, the user should pay attention to its popularity. Why? Other users contribute to the overall anonymity provided by the service, by using it a the same time. The more service is popular, the bigger the probability, that the user will be unnoticed in the crowd, as the provider cannot determine which sites were opened by which user. Yet popular serves have one flaw – a high amount of users equals lower bandwidth.
If you choose a VPN from another country than the one you occupy, be careful. In case of any illegal actions, you’re under the law of both countries.
Rule 1 – stay consistent
A user that wants to browse the internet safely, must remain consistent in his actions. That means if he’s searching the web using a VPN, he should do so every time. To be extra careful he should switch servers he uses. There’s little sense in a situation where a user browses a shady website with a VPN and then comes back using a standard connection. In that case, even if he’s hidden the data before, now they’re all visible to the receiver or an interceptor.
A safe VPN connection is commonly used in countries that have limited freedom of speech or while using services that assign its assets basing on geolocalisation. Good examples of services with those restrictions are YouTube and Netflix, where a user that has an active VPN with an IP address assigned to a certain localization might have access to local content. For example, if a user is connecting with an IP from the territory of US, the service will recognize him as a person from this territory and allow to receive all the content available in that particular localization.
VPN vs Legal systems
It’s worth to mention, that although VPN might ensure anonymity while using the web and indispose the third party to intercept the transmission, it has a significant weak spot. A company that delivers VPN services, if asked by authorities (f.e. police) is entitled to present any data gathered about its clients.
Anyone that cares about maximum privacy should consider choosing a provider that doesn’t collect users’ data and has servers located in a country that doesn’t respect the Geneva Convention, for example, Panama or Hongkong. Panama seems good as it doesn’t cooperate with other countries’ law enforcement agencies. We must remember, that VPN provides different IP address only from the perspective of the server we connect to.
Incognito mode
It’s a browsers’ feature, that allows using the internet without saving the data that the user leaves. It means no search history, cookies or browser history. Of course, the data we create will be visible for the receiver, but won’t be saved locally after ending the session. Therefore next user of the same device won’t have access to them.
Incognito mode is viable in public places or devices that are used by multiple users. For example, if you finish using a browser in the internet cafe, just close the page and no data will be stored in a browser’s memory. It’s strongly advised to use incognito mode while accessing pages that may contain sensitive data, for example, while logging to the bank account.
TOR network (The Onion Router)
TOR is a project aimed at preventing analysing web traffic. Its architecture refers to many layers of an onion. It enables anonymous communication by hiding a user’s localization and providing with hidden, anonymous services. Putting it simply, it’s a decentralized, multi-layer router network, that uses cryptography to cypher communication between them. A router at the beginning never directly sees the router at the end, only the nearest data provider/receiver from the next/previous communication layer. If somebody wanted to trace the communication, he’d only see the last intermediate router. There are, however, many items controlled by governments, that analyze that movement. This analysis combined with data from internet providers and knowing of logging time allows capturing criminals that thought they’re safe and unidentified.
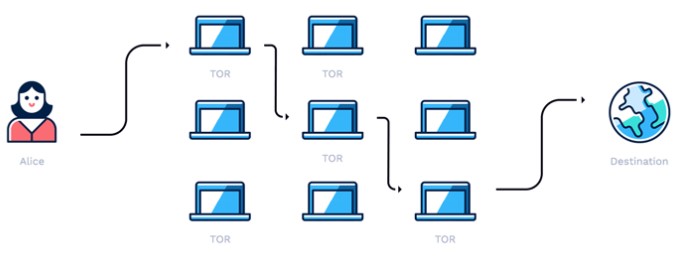
Fig. 2 TOR Network architecture
Using TOR Network is really simple and requires you to install TOR Browser. It’s a software based on Mozilla Firefox, that is used pretty much the same way. While browsing the internet, you get an anonymous IP address, that protects the user’s identity, leaves no trace and prevents from hacking. To maximize TOR’s potential it’s important to keep the Browser updated and don’t maximize the window, as it gives information about screen resolution.
Safe browsing with TOR
Connecting to TOR network with a TOR Browser allows to browse pages, but it has certain limitations that come directly from its specifics. JavaScript support is turned off, so many pages won’t work the way they’re meant to. Also turning it on will give out a significant amount of information about a user. Still, the browser is very user-friendly and intuitive. It connects automatically at the start. Since that moment very asset and every domain of the internet is accessible anonymously.
A very important aspect of the TOR network is the so-called Dark Net. It’s a hidden part of the internet, inaccessible from the standard browser. Darknet’s structure is based on particular server software, known as pseudodomain “.onion”. The most common services the Darknet offers are hidden websites, forums and marketplaces. They don’t always offer legal contents.
TOR network may be used for purposes that are considered illegal by some legal systems. Political criticism, copyrights violation, drugs, guns and pornography distribution – all those contribute to the Darknet’s aura of mystery and doubt. It’s worth to remember, that TOR’s main purpose is to keep users safe. Many TOR users obey the law and use the web legally. For others, it’s the only safe option to use the internet under heavy government censorship or human rights violation.
Tails (the Amnestic Incognito Live System)
Tails is a GNU/Linux (Debian) system distribution, that works as a live operating system DVD/USB. It’s meant to provide safe and anonymous use of the web. It consists of several tools and functions that will keep a user’s privacy while online. Tails’ main attribute its utility. Web browsers, communicators or email clients that are integrated with Tails system, are automatically configured with the launch of a system. The automatic mechanism that keeps you anonymous is based on the TOR network.
Tails operating system’s bundle includes:
- an anonymous TOR network witch Onion Circuits interface,
- TOR Browser,
- NetworkManager,
- Mozilla Thunderbird,
- Florence virtual keyboard,
- KeePassX password manager,
- MAT metadata anonymization tool.
ProtonMail
It’s an e-mail operator registered in Switzerland. What distinguishes it from thousands of other services is that it aims to keep its users anonymous. Its localization is non-contingent as the servers are under Switz law system jurisdiction. Therefore the data is inaccessible for other countries (such as US and NSA agency). The main advantage that contributes the most to the users’ privacy is automatic end-to-end encryption of every message. It means, that encryption takes place on the client’s side and it’s decrypted on the receiver’s side. Even ProtonMail’s employee cannot decipher the emails, not to mention any third party interceptors. Also, ProtonMail doesn’t gather any personal information while creating an account and assures that it doesn’t collect IP addresses and logging data, so they cannot be connected to the user’s account.
Temporary mailbox
Typing your email address on a website might cause some unpleasant consequences. Nobody likes receiving spam or malware emails just because he used his real email to comment on a forum section.
Temporary emails, also known as anti-spam mailboxes seems a great solution to this problem. Their main asset is no need to sign in and the content is restricted by time. They’re used mostly to register to services or forums that may be unsafe. They also work great as testing accounts.
While using anti-spam mailboxes you must remember that there are certain circumstances where they’re no good. Some services have temporary email blacklists and automatically prevent them from being used. I also suggest to don’t use them on websites where you want to have a working account. In case of losing the password, there might be a problem with recovering it. Temporary mailboxes don’t have passwords and are available for everyone, so if you have used one to create an account it might easily be taken over by someone that knows your temporary address.
Identity generators
Every user of the internet has found himself in a situation where he had to put some personal information in a form, for example, to use a certain feature or to download a pdf. file. What’s worse, in some cases the page asks you for sensitive information. Of course, you can take a while to make them up, but what to do when your session had a timeout and you have to put them again or if they don’t have proper validation?
Identity generators (personal data generators) are perfect for a situation like this. They are free to use and very fast in creating fictional information. They come in many forms, from a simple ID number generator to a full bundle containing a name, address, social security number, company name and credit card number.
Identity generators are useful in some cases, as they can keep your personal data safe, but they shouldn’t be overused. Using artificially generated data for, for example, banking agreements, is considered fraud and may cause a person to be held to account.
Don’t send document scans
A thing that might seem obvious is often not. We should never send copies of documents via the internet. Many people tempted by quick loan or an attractive job offer tend to send an ID scan to a person they don’t know. You never know what happens to them afterwards. They might fall into the wrong hands and be used to commit a crime. They might be processed with violation of GDPR or be sent between financial institutions employee. It might happen, that an employee that has access to clients’ personal information will be fired, so in an act of revenge, hell download them and sell to third parties. Generally, there’s a high risk of losing control over your documents and a stolen identity can cause a lot of problems.
Safety comes from wisdom
The tools I’ve mentioned are worth to use, although some rules must be followed. Most importantly be consistent in your actions. If you’re not cautious and don’t take care of your safety, sooner or later you’ll slip and let someone else obtain your data. A very basic mistake many users make is the inability to divide actions performed in anonymous web and those they perform in open internet. An excellent example of such practice is Ross Ulbricht, creator of Darknet forum Silk Road. He has committed a crime, but thanks to TOR network he was uncapturable. He made a serious mistake of using the same nickname in TOR as well as on the open internet. That led FBI agents to his real persona. After they’ve gathered solid evidence against him, he was prosecuted.
In the end, I’d like to say, that there’s more to say about the topic of anonymization. As I’ve mentioned at the beginning – different goals require different methods.
While writing this article I was aiming at presenting the case in the most accessible way. I’ve wanted to avoid tools that might lead to conflicts with law and point out possible risks.
Every internet user should be aware that staying anonymous is strictly connected to his approach and mindset. If you’re not consistent in what you do, no matter how sophisticated methods you use, you won’t be able to stay hidden.